Times Insider explains who we are and what we do, and delivers behind-the-scenes insights into how our journalism comes together.
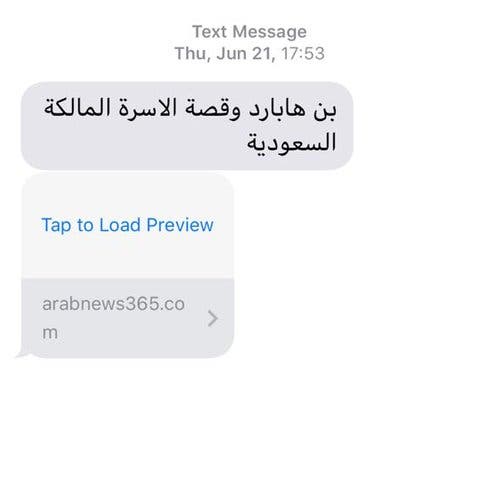
BEIRUT, Lebanon — On June 21, 2018, I received an Arabic text message on my cellphone that read: “Ben Hubbard and the story of the Saudi royal family,” with a link for a website, arabnews365.com.
I had been writing extensively about Saudi Arabia, including its royal family, and at first glance the link appeared to be a Saudi news story about my coverage — a subject that would normally grab my attention.
But it also struck me as fishy, so I refrained from clicking and decided to investigate. That led me to the booming market among governments for hacking technologies and a lesson in how easily the most intimate information on our phones — chats, contacts, passwords and photos — could become a target.
This type of hacking grabbed headlines last week in connection with a forensic report commissioned by Jeff Bezos, the owner of The Washington Post, that asserted with “medium to high confidence” that Mr. Bezos’ phone had been hacked after he received an encrypted video via WhatsApp from Mohammed bin Salman, the crown prince of Saudi Arabia.
Other technology researchers have questioned the report’s conclusions, but two United Nations experts gave it their stamp of approval, saying that the hack aimed to “influence, if not silence” The Post’s critical coverage of the kingdom.
The attempt on my phone, a month after the reported hack of Mr. Bezos, was less dramatic, but no less scary in its implications. An examination of my phone turned up no indications that it had been compromised, but technology researchers who inspected the message I received concluded that I was targeted with powerful software sold by NSO Group, an Israeli company, and deployed by hackers working for Saudi Arabia.
A spokesman for the Saudi Embassy in Washington did not respond to requests for comment.
When asked if its products had been used to target my phone, a spokesman for NSO Group said in a statement that it was “entirely deceptive” to suggest that its technology was responsible for all such phone hacking attempts, since other companies offered similar tools.
The researchers, at Citizen Lab at the University of Toronto’s Munk School, have in recent years identified 36 operators that have used NSO Group’s technology on hundreds of targets in 45 countries. These targets include four people whom the researchers were able to identify by name and could confirm were hacked by operators that appeared to be working for Saudi Arabia.
I was the fifth — and the first case the group had found of the technology being used against an American journalist.
As people have begun carrying more and more of their personal and professional lives on their phones, an industry has sprung up to sell tools to get that information. Many of the companies that sell the technology say they market only to governments for use in law enforcement and antiterrorism operations.
But critics, like the Citizen Lab researchers, say the lack of regulation of such technologies allows the companies’ often authoritarian customers to use the software against dissidents, activists, journalists and others.
The attempt on my phone came after I had covered Saudi Arabia for five years, most recently with a focus on Prince Mohammed, who had rocketed to power after his father became king in 2015.
Prince Mohammed was a lightning rod. His backers praised him for weakening the kingdom’s once-feared religious police, vowing to diversify the economy away from oil and lifting restrictions on women, while critics took him to task for cracking down on dissidents, coercing the resignation of Lebanon’s prime minister and locking hundreds of princes and businessmen in the Riyadh Ritz-Carlton on accusations of corruption.
I had written about all of those topics when my phone dinged one evening and I read the suspicious text message.
To figure out if it was malware, I first searched the web for the headline in the message, and found that the article didn’t exist.
Then I asked the editor of the real Arab News, an English-language newspaper in Saudi Arabia, if it used arabnews365.com.
“It is not us,” he replied.
The first tech security experts I consulted didn’t know what the message was but agreed it looked suspicious and warned me not to open the link. So I moved on, though I kept wondering what it was, who had sent it and why.
I got a clue a few months later when Citizen Lab published a report about Omar Abdulaziz, a Saudi dissident in Canada whose phone had been hacked with a text message similar to the one I had received.
Mr. Abdulaziz had political asylum in Canada and was well known in Saudi Arabia for criticizing its leaders on social media. He was also friends with Jamal Khashoggi, the dissident Saudi writer and Washington Post columnist who was killed and dismembered by Saudi agents in Istanbul in October 2018.
The report on Mr. Abdulaziz contained a table with domain names used by an operator that the researchers had determined was linked to Saudi Arabia. It included arabnews365.com.
I sent the message to Citizen Lab, whose researchers drew two conclusions.
First, since they had previously obtained a copy of NSO Group’s software, they were able to use it to scan the internet for connected servers and compile lists of web domains being used by various operators, including 20 that had pursued targets related to Saudi Arabia. One of these domains was arabnews365.com.
“We know for certain that the domain that was in the text was part of that command and control infrastructure that is connected to NSO Group,” said Ron Deibert, the director of Citizen Lab.
But determining who had used the software to send the message was harder, he said, and relied on circumstantial evidence.
“They don’t leave business cards when they do this kind of thing,” Mr. Deibert said. “This is something that is designed precisely to avoid detection.”
Citizen Lab concluded that this operator was connected to Saudi Arabia through a combination of the web addresses it used — some of which employed language that pointed to Saudi Arabia — and who its known targets were, said Bill Marczak, a Citizen Lab senior researcher.
So far, Citizen Lab has identified five people who were targeted by this operator. All five were targeted in May and June of 2018, and were involved in activities related to Saudi Arabia: Yahya Asiri, the head of a Saudi human rights organization based in Britain; an unnamed researcher for Amnesty International; Ghanem al-Masarir, a Saudi dissident with a sarcastic YouTube show; Mr. Abdulaziz, the Saudi dissident in Canada; and me.
“If the proposition is that one operator tried to hack all these people, what do they have in common?” Mr. Marczak asked. “The Saudi angle is it. There is really nothing else.”
Although the reported hacking of Mr. Bezos’ phone happened during this same period, it used a different technology: an encrypted video sent by WhatsApp, not a web address sent by SMS.
In his statement, the spokesman for NSO Group said it licensed its technology to law enforcement and intelligence agencies “under strict protocols and governance for proportionate operation for the sole purpose of preventing and investigating terror and crime.”
“Where misuse is alleged to have occurred, we have and will take action to investigate and suspend the capabilities,” the statement concluded.
Human Rights experts and campaigners argue that hacking technologies have become so powerful that governmental regulation is necessary to make sure they are being used ethically.
“We are facing a technology that is very difficult to track, extremely powerful and effective, and completely unregulated,” said Agnes Callamard, the United Nations special rapporteur on summary executions and extrajudicial killings, after the reported hack of Mr. Bezos’ phone. “That to me is unbelievable, that we have a technology that we absolutely cannot control or trace.”
She added that Mr. Bezos’ case should sound alarms because it took experts hired by one of the world’s richest men months to investigate what happened — a luxury most people don’t have. “It basically means that we are all extremely vulnerable,” Ms. Callamard said.
Follow the @ReaderCenter on Twitter for more coverage highlighting your perspectives and experiences and for insight into how we work.
Ben Hubbard’s first book, MBS: The Rise to Power of Mohammed bin Salman, will be published in March.