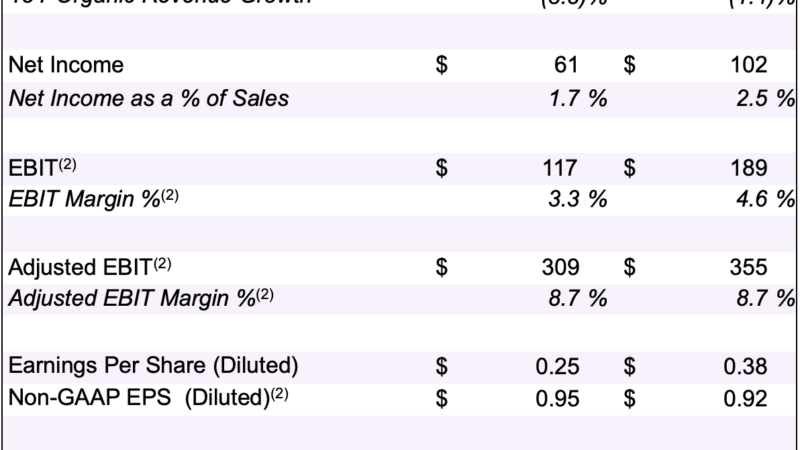
Latest technology could miss Australia due to encryption laws: Telstra – ZDNet

Telstra has warned that device vendors could skip Australia due to the nation’s encryption laws, leaving local companies uncompetitive.
With vendors usually sharing technical information with telcos before launching products in order to test them, Telstra said the requirements in the encryption laws compelling them to share that information with interception agencies could see Australia being skipped — as well as Telstra breaching its “contractual confidentiality obligations”.
“This has potential to adversely affect the competitiveness of Australian telecommunications providers in international markets and their ability to deploy the latest technology developments (e.g. new smart phones, artificial intelligence and IoT devices),” the company said in a submission to the Parliamentary Joint Committee on Intelligence and Security’s encryption law review.
“International vendors may also simply refuse to supply new technology or devices to Australian DCPs [designated communications providers].”
The Australian incumbent telco also called for immunities to be extended to any downstream third party providers. Telstra said secrecy provisions in the laws mean one of its suppliers could have had a notice issued and equipment modified, but the changes could make Telstra’s network or systems run slower.
“Such adverse effects could include service degradation, network faults, or other impacts on its business, or on non-target customers,” it said.
“While the immunity provisions of the framework would protect the DCP providing the assistance/capability under a TAR, TAN, or TCN, there is no protection for providers elsewhere in the supply chain if they (or their customers) are adversely impacted by the use of that ‘modified’ piece of equipment or software.”
Australia’s encryption laws — as defined in the Telecommunications and Other Legislation Amendment (Assistance and Access) Act 2018 that was passed in December 2018 — create three kinds of notices that a so-called “interception agency” can serve on what are called “designated communications providers”:
See also: Encryption laws are creating an exodus of data from Australia: Vault
- Technical Assistance Requests (TAR), which are “voluntary” requests for the designated communications providers to use their existing capabilities to access user communications;
- Technical Assistance Notices (TAN), which are compulsory notices to use an existing capability; and
- Technical Capability Notices (TCN), which are compulsory notices for a designated communication provider to build a new interception capability, so that it can meet subsequent TANs.
In a separate submission, a collection of industry groups — including the Communications Alliance, Australian Industry Group, Australian Information Industry Association, and Digital Industry Group Inc — reiterated many previous suggested amendments before the legislation was stranded before the May election.
The groups called for the use of warrants for the issuance of notices, the removal of TANs altogether, ensuring the legislation cannot be used to bypass the mandatory data retention or interception legislations, improving the consultation requirements for notices, and lifting the threshold for use of the encryption powers from crimes with a penalty of 3 years to 7 years.
The submission also called for clearer definitions throughout the legislation, particularly concerning “systemic weaknesses” and what can be constituted as a “whole class of technology”. It pointed to a prior submission to the committee from the Department of Home Affairs that said, “a class of technology encompasses: mobile communications technology [or] a particular model of mobile phone”.
“Using this broad definition, a weakness introduced in, say, all iPhone 8 sold in Australia (but not those sold overseas) would not constitute a systemic weakness unless the requesting agency ‘declared’ the class of technology to be all Australian-sold iPhone 8 rather than all iPhone 8 worldwide,” the industry groups said.
Read: Home Affairs says no problems with encryption laws even though local companies suffer
In an earlier submission, Vault Systems said it was being materially and detrimentally impacted by the encryption laws, even if it was just in relation to how the company is perceived.
“As foreign governments and customers are assessing against a ‘media headline test’, we are in an unfortunate position where logical persuasion is not sufficient to counter perception,” Vault said in its submission.
“We are currently seeing an exodus of data from Australia including physical, operational, and legal sovereignty.”
The cloud provider said based on the size of the Australian market, and its “perceived compliance burden”, it has seen multinationals blacklist the nation, even when the same company operates in China and Russia.
The industry groups said they were concerned the committee had not “sufficiently considered” the impact of the laws on Australian exporters.
“This issue is not the result of a global misunderstanding of the workings of the Act, as has been suggested in at least one submission to the Committee,” they said.
“Rather, the damage being done to Australian industry is due to technology buyers and investors around the world having listened to the strong body of international and Australian expert opinion on the risks that the Act creates for the security of Australian-manufactured technology equipment and systems.”
Related Coverage
Encryption laws are creating an exodus of data from Australia: Vault
Detrimental effects are both real and perceived, according to Australian cloud provider.
Amazon asks for clarification of data retention requirements under Australia’s encryption laws
The technology giant is concerned the Act does not make it clear if it is subject to the data retention obligation under Australia’s encryption laws.
Optus gained exemption to store metadata unencrypted
Use of legacy applications allow Optus to seek an exemption from the rules.
Home Affairs says no problems with encryption laws even though local companies suffer
The department said it is however ‘focused’ on addressing the negative perception of Australia’s encryption laws, saying companies actually lack a clear understanding of the obligations within legislation.
Employees not the target of encryption laws: Home Affairs
Australian developers really do need to relax. Cops and spooks are being told very clearly that the Assistance and Access Act isn’t for dragooning you into deceiving your bosses.