On April 27, a woman in eastern Brooklyn called the police. She told them that just before sunrise, at 5:50 a.m., her ex, John, confronted her on the street with a gun.
The two were scheduled to appear at a court hearing over who would get possession of an apartment they once shared. The woman told police that John had said, “Shut the [expletive] up. You better not go to court,” pushed her to the ground and repeatedly punched her legs.
The woman already had a protective order in place against John. The next day, the police arrested him and charged him with assault, witness intimidation and other crimes.
John told his lawyer, a public defender, that he was innocent. He said that at the time in question, he’d been on his way to work in a different neighborhood in Brooklyn. But he hadn’t arrived there until 6:40 a.m. It was possible that he’d committed the assault and then made his way across the borough.
John was scared. Without proof of his whereabouts, he’d be fighting an uphill battle against the state. Innocent people often take plea deals because it’s easier than proving they’re innocent. He thought about losing his home and going to prison.
John’s lawyer, Jeffrey Sugarman of the Legal Aid Society of New York City, asked his client a deceptively simple question: Do you have a smartphone?

In America, citizens accused of crimes are supposed to have an advantage. The burden of proof is on prosecutors, and the government must turn over all its evidence to defendants, who have no reciprocal obligation.
In practice, of course — and especially when defendants don’t have a lot of money — the government has the edge. Investigators can issue subpoenas, compel testimony and pressure defendants into pleas. Today, one way in which the deck is stacked against defendants involves technology.
This tech gap has two basic forms. First, law enforcement agencies can use warrants and court orders to compel companies to turn over emails, photos and other communications, but defense lawyers have no such power. And second, the government has access to forensic technology that makes digital investigations easier. Over the last two decades, the machines and software designed to extract data from computers and smartphones were primarily made for and sold to law enforcement.
Initially, investigators and prosecutors used such technology mostly to gather evidence about computer crime and child pornography. But now digital forensics can play a role in virtually any case, because the data inside our Facebook accounts, smartphones and devices we wear on our bodies contains so much of our day-to-day movements and communications.
To successfully defend its clients, the Legal Aid Society, New York City’s largest public defender office, realized in 2013 that it needed to buy the same tools the police had: forensic devices and software from companies including Cellebrite, Magnet Forensics and Guidance Software. Not only does the expensive technology unearth digital evidence that is otherwise hard or impossible to find, it captures it in a format that can hold up in court, as opposed to evidence that could have been tampered with or forged. A properly processed device can yield emails, text messages, call logs, location history, photos, metadata and more — even material that has been deleted.
The Legal Aid Society’s New York forensic lab is a rarity in the world of public defenders, because most tightly budgeted offices simply can’t afford it. The bill for the equipment was approximately $100,000 — a fortune in a public defender’s budget, but a small amount by the standards of the Manhattan district attorney’s office, which in 2016 built a forensics lab for $10 million.
On a Wednesday in May, John — whose lawyer asked that his last name be withheld — went to the Legal Aid Society’s TriBeCa office, stuck between Gap’s headquarters and a preschool. He handed his Android phone to one of the organization’s six forensic analysts, Brandon Reim.
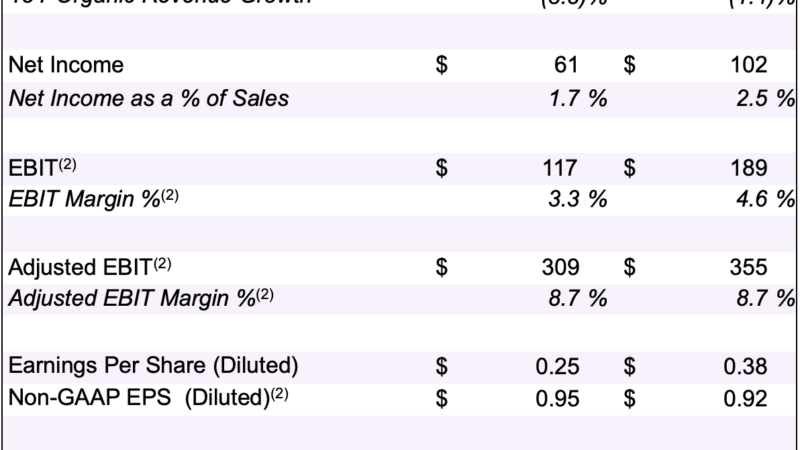
Mr. Reim wanted to reconstruct John’s movements on the morning of April 27. He plugged the phone into a hand-held tablet, called the Touch2, made by the Israeli company Cellebrite. Known as a universal forensic extraction device, the Touch2 is able to pull data from almost any gadget and preserve it in a format that courts will accept as evidence. Mr. Reim also used a Cellebrite software program called Cloud Analyzer to reach John’s data on Google’s servers. After a few hours, Mr. Reim found what he was looking for: Google had logged more than 100 location points, with latitude and longitude, for John’s phone during the period when he had supposedly threatened his ex.
A spokesman for Cellebrite, Christopher Bacey, said the company does not disclose its prices. But government budgets offer up some transparency. The Touch2 can cost $10,500 with a $3,100 annual maintenance fee, while Cloud Analyzer can go for $7,999, with an annual fee of $2,625.
At the Legal Aid Society, Mr. Reim and his fellow analysts are searching for data to support clients’ claims of innocence. But if the data instead implicates the client, that’s valuable, too — it helps public defenders understand the strengths or weaknesses of their cases and decide whether to negotiate a plea.
Google’s minute-by-minute accounting of John’s whereabouts, which might seem dystopian in a different context, proved beneficial because it confirmed his story. He left his house at 5:10 a.m. to take the subway to work. At the time of the supposed assault in eastern Brooklyn, he was five miles away.
Mr. Reim plotted John’s movements on a Google map. Mr. Sugarman showed it to the assistant district attorney, who quickly dismissed the case.
As forensic technology has advanced, many constituencies beyond law enforcement have come to enjoy its power — the armed services, intelligence agencies, even corporate investigative outfits. Public defenders and citizens accused of crimes remain an afterthought. When I sent an inquiry to Cellebrite about how its products “get used by the defense instead of by law enforcement,” its spokesman assumed I was talking about the military.
There are dozens of forensic devices on the market. The Department of Homeland Security has tested many of them to report how well they do what they claim. Cellebrite, which has promoted its ability to break into locked phones, is one of the industry’s biggest names. Grayshift, founded by a former Apple engineer, makes a product called GrayKey that has allowed law enforcement agencies to break into and extract data even from encrypted iPhones. There’s also Magnet Forensics, which has offices in the United States, Canada, the Netherlands and Singapore; Black Swan Digital Forensics, based in Memphis, which advertises a “remote extraction” service for around $500 a pop; and OpenText, which recently acquired the California-based Guidance Software, which was one of the first to start making forensic software, back in 2002.
Though public defenders aren’t their typical customers, most forensics companies are willing to sell to them. Not Grayshift. A public defender who contacted the company this year with a sales inquiry was told that Grayshift “is tightly controlling the sales and distribution to local, state, and federal government law enforcement end-users only.” (The company did not respond to a request for comment.)
At least public defenders know that GrayKey exists. For years, that wasn’t the case with so-called I.M.S.I. catchers (for international mobile subscriber identity), better known as StingRays. These devices, made by the Harris Corporation, impersonate cell towers to intercept texts, calls, emails and other data; they can also locate cellphones and thus the people using them. Harris has required law enforcement agencies to sign nondisclosure agreements when they buy the devices, and for years, police and prosecutors hid their existence from defense attorneys. The secret wasn’t exposed until one tech-savvy California tax defrauder became obsessed with finding out how the police had found him.
Forensics experts have helped law enforcement acquire even the most daunting digital evidence. After a December 2015 mass shooting in San Bernardino, Calif., the F.B.I. asked Apple to help it get into a locked iPhone. Apple refused, on the grounds that it would undermine the security of their products. The F.B.I. ended up paying an unnamed third party to break into the device.
“It’s definitely an uneven playing field,” said Jennifer Mnookin, the dean of the law school at the University of California, Los Angeles. “Law enforcement has an understandable desire to extricate data from the digital world to solve cases, but there hasn’t been adequate scrutiny of these new techniques.”
Ms. Mnookin described a recurring pattern: Law enforcement agencies get a new investigative technique — fingerprinting, DNA analysis, breathalyzer tests — and those representing the accused struggle to play catch-up. Developing the new technical expertise necessary to adequately defend their clients is a challenge. Not only do public defenders tend to be underfunded, law enforcement can monopolize the experts in the field and forbid them from working for the defense.
Jim Kouril, a forensic analyst who worked as a police officer in Idaho for 24 years before joining the public defender’s office, said his former colleagues viewed his career move as going to work “for the dark side.” But his new position was hardly glamorous. “The big discrepancy between law enforcement and public defense is resources,” Mr. Kouril said. “I had everything I wanted in law enforcement: high-powered computers and equipment. Now, it’s like pulling teeth.”
In a review of public defender offices across the country, The New York Times found no other organization with a forensics operation comparable to the one in Manhattan. A handful of offices — in Pima County, Ariz.; Cook County, Ill.; and Canyon County, Idaho — recently bought one extraction device or have an internal expert. The public defender’s office in Philadelphia has started building a dedicated lab. But most public defenders have to hire private consultants to conduct forensic examinations of the evidence in their cases. This is a costly exercise that requires people to give up their phones for at least a week — an impossible request in some cases, particularly when it’s a third party involved in a case and not the defendant.
Otherwise, public defenders can get this digital evidence only if law enforcement chooses to examine a device. (Most agencies have no trouble getting access to the technology. A police force or prosecutor’s office that lacks internal resources can reach out to the nearly 350 shared cybercrime labs across the country for help.) If a case goes to trial — a vanishingly rare occurrence, as the vast majority of defendants in federal and state cases alike take plea bargains — a public defender might get a forensic report turned over. But these reports can be thousands of pages long, easily navigable only if you have a forensic company’s proprietary software.
Jerome Greco, a New York public defender who came to specialize in technological evidence partly because of an interest in hacking as a teenager in New Jersey, runs the Legal Aid Society’s forensic lab. He says the unit has proved invaluable in the early weeks of new cases, preventing clients from being formally charged or getting them out of jail when digital evidence makes their innocence clear.
“Americans spend so much more time on their phones now. And the amount of information and value of digital information has dramatically increased as a result,” said Mr. Greco. “Law enforcement is onto that. But so are we.” He added, “Our goal is to push back against law enforcement’s technological advantage.”
Geoff Burkhart, who oversees the public defender system in Texas, said that his colleagues barely have case-management software, let alone forensic equipment, and that the budget to hire outside forensic experts is minimal. “All the tough-on-crime years, all the funding went into prosecution and policing, while funding for public defense stayed stagnant,” said Mr. Burkhart. “So public defenders’ caseloads went up, but their funding didn’t.”
Public defenders are also at a disadvantage to prosecutors when it comes to interacting with big tech companies. A 1986 law, the Stored Communications Act, requires that law enforcement agencies obtain a warrant to get access to emails, private messages and other data kept on companies’ servers. Public defenders are held to the same standard, even though they can’t get warrants; they can only issue subpoenas, which limit them to asking for information about users, not the content of their digital activity.
Facebook and Google “are terrible to work with,” said Joel Simberg, a public defender in Cook County. “The state’s attorney and police get great information, but we get turned down all the time. They tell us we need to get a warrant. We can’t get warrants. We have subpoenas, and often they ignore them.”
Facebook, Google and Twitter have special online portals for law enforcement agencies, which make it easier for them to request information from users’ accounts. But there are no equivalent portals for public defenders. When Mr. Greco, in New York, wants to send a subpoena to Facebook, he has to get a judge to sign off on it in California and hire a server to deliver it in person to the company’s office in Menlo Park.
“They make it supereasy for law enforcement and superhard for everyone else,” said Mr. Greco. “They should make portals for public defenders.”
“People expect us to keep their information private, and we believe strongly that federal law requires us to do so,” said a Facebook spokeswoman, Rochelle Nadhiri, by email. “That’s why we have strict guidelines for sharing information in response to requests for their information.”
In a forthcoming article for the U.C.L.A. Law Review, Rebecca Wexler, an assistant professor of law at the University of California, Berkeley, argues that “exceptions to privacy laws that enable law enforcement to access sensitive information should also apply to criminal defense investigators.”
Ms. Wexler cites the case of Lee Sullivan and Derrick Hunter, two California men accused of murder. “Sullivan tried to subpoena Facebook, Twitter, and Instagram for private messages that would show that the sole witness who placed him at the scene was lying, but the companies refused to comply, arguing that a federal privacy law from 1986 prevented it,” Ms. Wexler writes. “That left Sullivan and co-defendant Derrick Hunter in jail six years awaiting trial without key evidence to test the credibility of the witnesses against them.”
A judge ordered the companies to hand over the data earlier this year, but they resisted; he held them in contempt in July. “Facebook and Twitter have made it clear that they are unwilling to alter their behavior, regardless of the harm to others — or the rulings of this court,” the judge, Charles Crompton, wrote.
Giovanna Falbo, a spokeswoman for Twitter, said, “We have taken a stand against the state court’s order in this case because we believe that it violates the federal Stored Communications Act and undermines a key purpose of that law — to protect individuals’ privacy rights in electronic communications.”
Al Gidari, the director of privacy at Stanford Law School, said that the Stored Communications Act prevents defense lawyers from using subpoenas to harass witnesses, victims or police officers by obtaining their personal information. He has long pushed for a federal rule change that would allow judges to force prosecutors to write warrants on behalf of defense lawyers who have proved certain evidence is vital to collect.
Jeffrey D. Stein, a public defender in Washington, D.C., recently wrote an opinion piece for The Washington Post on the subject of exculpatory evidence remaining trapped online. “Innocent people will continue to be vulnerable to conviction, not because evidence of their innocence doesn’t exist, but because the law doesn’t permit them to reach it,” he argued.
“Funding is always the obstacle, [but] this should be mainstream across the country,” said Tina Luongo, the lawyer who founded the Legal Aid Society of New York City’s forensic lab. “It’s the clients’ constitutional right. It exonerates our clients and helps us bring them justice.”
Aaron Krolik contributed reporting.